In an era where data breaches and cyber threats are becoming increasingly common, protecting sensitive company data has never been more critical. Traditional security measures, while effective to some extent, are often not enough to safeguard against modern threats. Zero Trust Network Access (ZTNA) has emerged as a robust solution, designed to secure sensitive information by adhering to the principle of “never trust, always verify.” This article explores the role of ZTNA in protecting sensitive company data, its benefits, implementation challenges, and why it is essential for modern businesses.
Understanding ZTNA
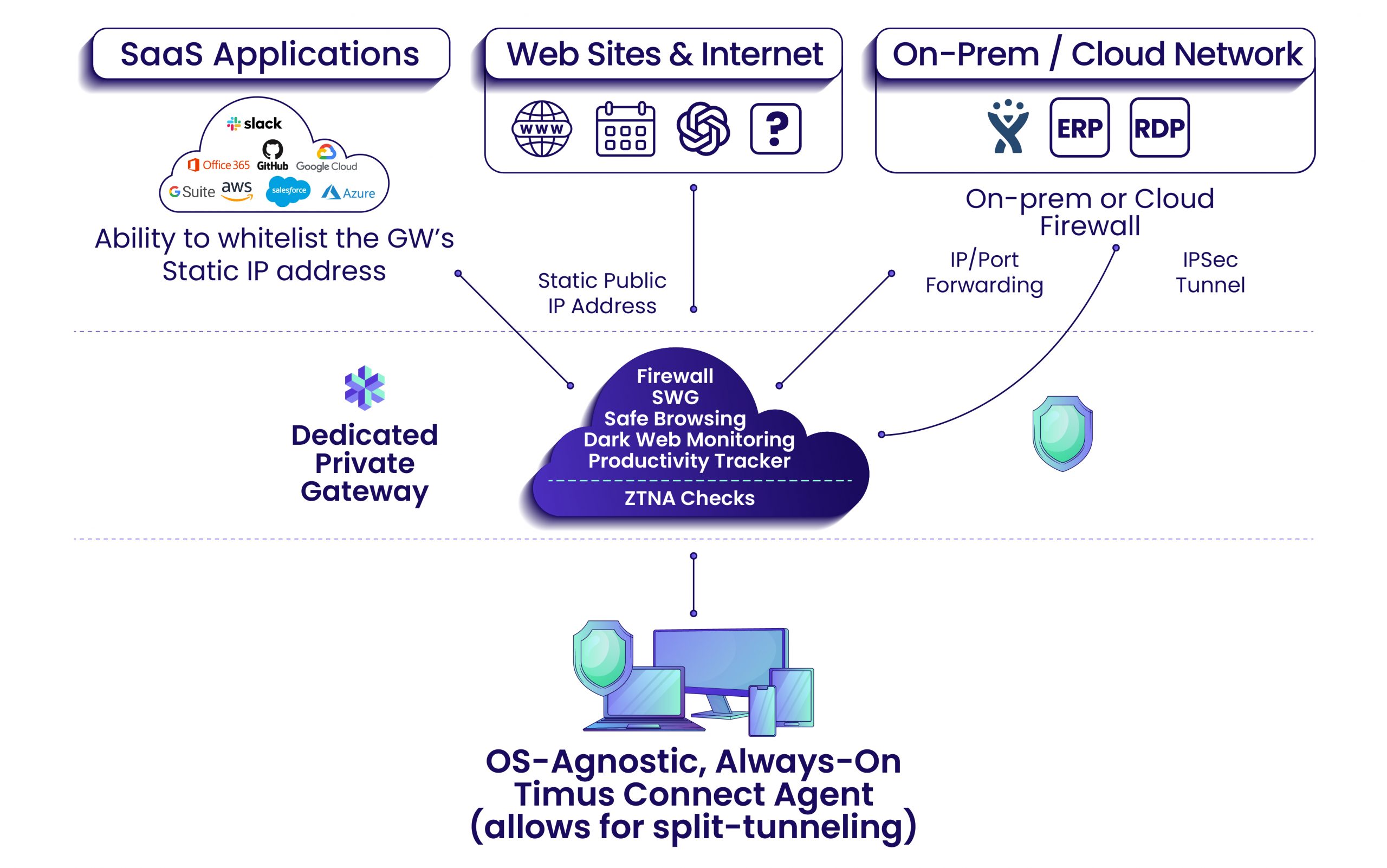
What is ZTNA?
Zero Trust Network Access (ZTNA) is a security model that ensures that only authenticated and authorized users can access specific resources within a network. Unlike traditional security models that operate on the assumption that everything within a corporate network can be trusted, ZTNA operates under the assumption that threats can come from both inside and outside the network. ZTNA requires continuous verification and does not grant implicit trust to any user or device, regardless of their location.
How Does ZTNA Work?
ZTNA works by creating a secure, encrypted connection between the user and the resource they are accessing. It enforces granular access control, ensuring that users only have access to the data and applications they need for their roles. ZTNA solutions typically rely on identity verification, device posture assessment, and real-time context to determine whether a user should be granted access.
The Importance of ZTNA in Data Protection
Mitigating Internal and External Threats
One of the primary advantages of ZTNA is its ability to mitigate both internal and external threats. Traditional security models often focus on protecting the perimeter of the network, leaving internal threats unchecked. ZTNA, on the other hand, ensures that even if an attacker manages to breach the perimeter, they will not be able to access sensitive data without passing through multiple layers of verification.
Enhancing Access Control
ZTNA enhances access control by enforcing the principle of least privilege. This means that users are only granted access to the resources they need to perform their jobs, reducing the risk of unauthorized access to sensitive information. This level of control is especially important in industries where data sensitivity is paramount, such as healthcare, finance, and government.
Protecting Remote Workforces
The rise of remote work has introduced new challenges for data security. Traditional VPNs, while useful, often provide broad access to the network, which can be exploited by cybercriminals. ZTNA addresses this issue by providing secure access to specific applications and data, regardless of where the user is located. This makes it an ideal solution for companies with a distributed workforce.
Key Benefits of ZTNA
Improved Security Posture
By implementing ZTNA, companies can significantly improve their security posture. The continuous verification process ensures that only legitimate users can access sensitive data, reducing the risk of breaches. Additionally, ZTNA’s ability to segment the network and limit access helps to contain potential threats, preventing them from spreading across the network.
Simplified Compliance
Compliance with data protection regulations is a significant concern for many businesses. ZTNA simplifies compliance by providing detailed access logs and audit trails, which can be used to demonstrate adherence to regulatory requirements. The granular control over data access also ensures that sensitive information is only accessible to authorized users, further aiding compliance efforts.
Scalability and Flexibility
ZTNA solutions are highly scalable and can be easily adapted to meet the needs of growing businesses. Whether a company is expanding its workforce or adopting new cloud-based applications, ZTNA can be quickly scaled to provide secure access to additional resources. This flexibility makes ZTNA an attractive option for businesses of all sizes.
Challenges in Implementing ZTNA
Integration with Legacy Systems
One of the main challenges in implementing ZTNA is integrating it with existing legacy systems. Many companies still rely on outdated infrastructure that may not be compatible with modern ZTNA solutions. Overcoming this challenge requires careful planning and potentially investing in upgrades to ensure a seamless transition.
User Experience
While ZTNA enhances security, it can also introduce friction into the user experience. The continuous verification process, while necessary, may be seen as a hindrance by users, especially if not implemented correctly. Companies must strike a balance between security and usability to ensure that ZTNA does not disrupt business operations.
Cost Considerations
Implementing ZTNA can be costly, particularly for small and medium-sized businesses. The cost of deploying ZTNA solutions, training staff, and maintaining the system can add up quickly. However, the long-term benefits, such as reduced risk of data breaches and simplified compliance, often outweigh the initial investment.
The Future of ZTNA
Adoption Trends
As cyber threats continue to evolve, the adoption of ZTNA is expected to increase. More businesses are recognizing the limitations of traditional security models and are turning to ZTNA to protect their sensitive data. The growing demand for secure remote access solutions is also driving the adoption of ZTNA, especially in the wake of the COVID-19 pandemic.
Innovations in ZTNA
The ZTNA landscape is continually evolving, with new innovations aimed at enhancing its effectiveness. These include advancements in AI and machine learning, which can be used to predict and prevent potential threats, and improvements in user experience, such as faster authentication processes and more intuitive interfaces.
Conclusion
In a world where data breaches are becoming increasingly common, the need for robust security solutions has never been more pressing. ZTNA offers a comprehensive approach to protecting sensitive company data by enforcing strict access controls and continuously verifying the identity of users. While implementing ZTNA may present challenges, the benefits it offers in terms of improved security posture, simplified compliance, and scalability make it a worthwhile investment for businesses of all sizes. As cyber threats continue to evolve, ZTNA will play an increasingly important role in safeguarding sensitive information and ensuring the resilience of modern businesses.